Film critic Jeremy Scott from Cinema Sins takes a look at all of the "movie sins" in Pixar's 2017 animated fantasy film, Coco...(Read...)
Read the full article here by Likecool
Film critic Jeremy Scott from Cinema Sins takes a look at all of the "movie sins" in Pixar's 2017 animated fantasy film, Coco...(Read...)
Today Glitch, the “friendly community where you’ll build the app of your dreams”, is officially “tearing off the beta label”. To celebrate, they’ve made a major announcement each day this week.
The announcements include Glitch for Teams, “Making Learning to Code More Accessible” by adding embed support, “Tackling the Biggest Pain Points in Web Development” by adding things like “full-stack view source”, “Reinventing Version Control with Glitch Rewind”, and open-sourcing the Glitch.com app which will allow the community to remix the site to suggest ideas.
Glitch is super exciting to me. Their efforts to make development more accessible, appealing, and fun will likely have profound effects on the community in the coming years.

Grazie alla collaborazione con Riccardo Burchielli, uno dei più noti illustratori del mondo sci-fi, e Giulio Gualtieri, sceneggiatore e editor in chief di grandi progetti, nasce We Race, un web comic che racconta la storia di un giovane pilota in gara con se stesso e che affronta una grande sfida.
In un universo sospeso nel futuro, prende forma la storia di una passione che attraversa le epoche, senza conoscere limiti: perché il mondo può cambiare, ma le emozioni restano le stesse.
Non resta che scoprire i primi due episodi on line: sito web, pagina Facebook.
After starting with Ubuntu, Microsoft has added a number of Linux distributions to its Windows Subsystem for Linux (WSL) Linux runtime environment. A Windows machine can simultaneously offer an Ubuntu, SUSE, Debian, and Kali "personality," providing users with a choice of the different distributions' preferences and package management.
But if your distribution isn't yet available or if you want a Linux installation that's customized just the way you like it, there's now an answer: Microsoft has an open source tool for building your own Linux package. The tool is aimed at two groups: distribution owners (so they can produce a bundle to ship through the Microsoft Store) and developers (so they can create custom distributions and sideload them onto their development systems).
Neat.
I'm hiring JS developers and data scientists to join me in my new start-up, Yelda. We're building a Virtual Assistants platform to allow all companies in the world to activate their assistant in a minute. Join us now ! It's only the beginning of the Age of the Assistance, we've the same feeling than when we were building the first web CMS in the early 2000's!
Thomas Gx, CommitStrip founder & Yelda CEOJe recrute des développeurs JS et des data scientists pour me rejoindre dans ma nouvelle start-up, Yelda. Nous construisons une plateforme d'assistants virtuels qui permet aux entreprises d'activer leurs assistants en quelques minutes. Rejoignez-nous, c'est le moment ! Ce n'est encore que le début de l'Ère de l'Assistance, on a les mêmes sensations que quand on on développait les premiers CMS web au début des années 2000 !
Thomas Gx, CommitStrip founder & Yelda CEOWith the new G Pro headset, Logitech set out to make something that gamers could wear for hours on end, without getting fatigued. It's a fairly straightforward pair of headphones: It only offers stereo sound (no fancy surround option), and it relies on an analog audio connections. Instead of the sports mesh headphone material found on Logitech's other gaming headsets, though, the $90 G Pro sports soft leatherette. The company claims it offers 50 percent more sound isolation than before, but more importantly, the new material simply feels better. (The previous covering made my ears feel a bit itchy after a few Overwatch matches.)
The headphones feature Logitech's Pro-G drivers with a slightly more aggressive sound profile than last year's headsets. While I found the G433 and G533 to sound a bit flat, the G Pro accentuate bass, which makes plenty of gaming moments feel more satisfying. Some music fans prefer a neutral sound profile, but when it comes to games, that tends to sound dull. The G Pro comes with a removable microphone, which features noise-canceling and better sensitivity than past Logitech offerings. You'll need a separate microphone jack to take advantage of that feature, which could be a problem for some gaming laptops.
Logitech says it developed the G Pro based on feedback from eSports players, and it shows. In addition to the leatherette ear coverings, you've also got microsuede replacements in the box. While I missed the useful noise separation from Logitech's surround sound headphones, the G Pro still sounded excellent. I could easily make out the careful footsteps of other players looting gear in Playerunknown's Battlegrounds, or enemies creeping up behind me in Overwatch. I also found myself paying more attention to games than with Logitech's previous headsets, thanks to the improved sound isolation.
At $90, the G Pro sits in the middle of Logitech's gaming headphone lineup, but they're a solid pick if you're looking for a high-quality wired option. You'll be able to snag one of your own in April.
Read more of this story at Slashdot.
Valve is preparing to make another significant open-source code contribution in the very near future.
Valve developers are working on open-sourcing their Steam Networking Sockets library. This library is a basic network transport layer for games with a TCP-inspired protocol that is message-oriented, built-in re-transmission for greater reliability, bandwidth estimation, supports encryption, and will handle other features needed for a practical networking layer by modern games.
The SteamNetworkingSockets library is currently used by Counter-Strike: Global Offensive, Dota 2, and other games on Steam. This networking sockets library will be able to function independently of Steam and is being released under a three-clause BSD license.
It will be interesting to see how well this game networking sockets library works once the code is made available compared to the many other existing game networking libraries already available and several open-source projects, but should prove to be useful with it being good enough for CS:GO and other Steam multi-platform games.
Update:The initialized Git repository is at
GameNetworkingSocketsalbeit the code drop has yet to happen.
From the Appbase.io team:
We started building dejavu with the goal of creating a modern Web UI (no page reloads, infinite scroll, filtered views, realtime updates) for Elasticsearch with 100% client-side rendering so one can easily run it as a hosted app on GitHub pages, as a Chrome extension or as a Docker image.
Try it for yourself.

Amid the torrent of news at CES in January, it was easy to miss the unveiling of NVIDIA's Drive platform -- a way for the company to test out its self-driving algorithms through repeated simulations. At that point, it was more of a concept than an actual product. Today, the company revealed its Drive Constellation system, a multi-server setup that'll let its partners run those self-driving simulations on their own. Think of it as The Matrix for autonomous algorithms: It's a way to train those vehicles to deal with extreme situations, without endangering anyone in the real world. The news comes after NVIDIA announced that it'll be pausing its self-driving testing on roads, following last week's fatal Uber self-driving accident.
On stage at the company's GPU Technology Conference (GTC) today, CEO Jensen Huang described self-driving as "probably the hardest computing technology we've ever encountered." But, after the Uber accident, he says he was reminded just how important this work is. "We have to solve it step by step by step," Huang said. "We're dedicating ourselves to this problem. The grandest of computer problems."
On one end of the Constellation system is a server running NVIDIA's Drive Sim software. As you'd probably guess, it simulates all of the technology you'd find on a self-driving car, including sensors, cameras, radar and lidar (the light and distance measuring component). It's powered by the company's GPUs, each of which creates its own stream of sensor data. The simulation server can also render "photoreal data streams" to reflect all sorts of driving conditions, like a fierce blizzard or glare during a sunset.
Another server is powered by the company's Drive Pegasus software, which runs all of NVIDIA's autonomous car technology and processes the incoming sensor data. The Pegasus server sends its responses back to the simulation machine for validation. That feedback loop occurs 30 times a second, according to NVIDIA.
Using this dual server setup, car makers will be able to construct all sorts of extreme scenarios to see how their self-driving algorithms react. The obvious drawback is that it's tough to simulate every potential issue, but it's still better than relying entirely on real-world testing (especially since it can easily be run millions of times per day).
Like any machine learning algorithm, NVIDIA's self-driving technology will only get better with every simulation. At CES, the company unveiled its Xavier system-on-a-chip, which will let other companies quickly build up their own autonomous vehicles. NVIDIA says early access partners will get access to the Drive Constellation platform in the third quarter of this year.

NVIDIA will suspend all of its public road self-driving tests following Uber's fatal accident, a company spokesperson has told Recode. The company supplies chips for Uber's self-driving vehicles and it says that it needs to find out more about last week's crash. "The accident was tragic," a spokesperson said in a statement. "It's a reminder of how difficult [self-driving car] technology is and that it needs to be approached with extreme caution and the best safety technologies."
During his keynote today at NVIDIA's GPU Technology Conference, CEO Jensen Huang said the fatal accident reminded the company how important safety is when it comes to this type of technology. "It's hard," he said. "Safety is the single most important thing. It's really hard technology, it's probably the hardest computing technology we've ever encountered." He added that NVIDIA was dedicating itself to improving safety calling it "the grandest of computer problems." He didn't mention, however, that the company was suspending its self-driving tests.
Uber halted its testing following last week's accident as did Toyota and nuTonomy. Yesterday, Arizona's governor suspended Uber's ability to test its self-driving vehicles on the state's public roads. "Improving public safety has always been the emphasis of Arizona's approach to autonomous vehicle testing, and my expectation is that public safety is also the top priority for all who operate this technology in the state of Arizona," Governor Doug Ducey said in a letter. "The incident that took place on March 18 is an unquestionable failure to comply with this expectation."
Tempe's police chief has said that Uber was likely not at fault in the fatal crash.
Today, NVIDIA announced its Drive Constellation system -- a multi-server setup that will let autonomous vehicle developers test their algorithms through virtual simulations rather than real-life evaluations.
Via: Recode
While FreeBSD has a Linux compatibility/emulation layer that
allows it to run some Linux games, an independent community developer has been working on porting Epic Games' Unreal Engine 4 to FreeBSD.
FreeBSD developer "malavon" has been porting the Unreal Engine 4 game engine to FreeBSD and in the process getting most of the tech demos / code samples to build.
With this being an unsanctioned port, the support isn't destined for Epic Games' official code-base but is available via the developer's personal repository. The test target has been FreeBSD 11.1 AMD64.
More details on this in-progress Unreal Engine 4 port via
this FreeBSD.org forum thread. The Phoronix reader who tipped us off to this work was able to try the it and confirm they are in fact working.
GNOME contributor Yussuf Khalil has managed to uncover and resolve a bug in Clutter that was hurting GNOME's performance.
The developer has begun analyzing GNOME performance issues and one of the first things he uncovered were frequent spikes in GNOME's frametimes at regular intervals. He ended up finding out that the frequent spikes were caused by showing the seconds on the clock within GNOME Shell.
While not showing the seconds on the time make the large spikes in frame time go away, he uncovered the root cause within Clutter's text rendering code. Yussuf discovered that whenever the text changed, the layout of the text was recalculated. In the case of seconds on a clock, the layout though obviously should never need to change. With his minor patch, Clutter now checks to see if the size of the text is the same as before, if so only a redraw is triggered and not the entire re-layout process.
With this fix, the median frame-time drops from 16.97ms to 12.97ms.
The fix has been
mergedfor GNOME 3.30 though there is also a request to get it back-ported to GNOME 3.28.
Coming up in May is a GNOME Performance Hackfest in Cambridge, so there will hopefully be more performance improvements to pass along for GNOME 3.30.
Last week Intel
announced their open-source sound firmware projectwhile the latest project in the open-source realm comes via the Linux Foundation with the launch of OpenBMC.
The Linux Foundation is backing the OpenBMC project community with a goal of creating an open-source baseboard management controller (BMC) firmware stack that can be used across motherboards and computing environments.
IBM is contributing the initial code for OpenBMC and among the other organizations getting behind this initiative are Google, Facebook, Intel, and Microsoft. Among the reasons for working on OpenBMC are growing cloud deployments making conventional BMC software less practical. Having an open-source BMC software stack can also improve the security of the system as well as offering new configuration and monitoring potential.
The OpenBMC project should be appearing shortly at
OpenBMC.org.
Read more of this story at Slashdot.
ostechnix: Terminus - A cross-platform, open source, web technology based Terminal for modern age, inspired from Hyper.
Read more of this story at Slashdot.
DragonFFI is a foreign function interface (FFI) built using the LLVM and Clang compiler stack to provide a library calling C functions and C data structures that can be used from any other programming language.
At this stage DragonFFI supports Python 2 and Python 3 from Linux/macOS and Python 3 on Windows. The DragonFFI implementation is designed to overcome shortcomings of other FFI implementations like libffi and cffi by its use of LLVM/Clang. This work also includes supporting on-the-fly compilation of C functions.
Moving forward they are looking at adding another foreign language interface with JavaScript and Ruby being two of the mentioned contenders. The lead developer also talks of possibly JIT'ing code from the final language to native function code in the future too.
Those wanting to learn more about DragonFFI can do so via
this LLVM blog post. The code to DragonFFI is currently hosted on
GitHub.
Security researchers with Israel-based CTS-Labs, have discovered a staggering thirteen critical security vulnerabilities for AMD's "Zen" CPU microarchitecture, which are as damning as the recent "Meltdown" and "Spectre" vulnerabilities that affect various CPU manufacturers at varying degrees (Intel, AMD, and ARM). The thirteen new CVEs are broadly classified into four groups based on the similarity in function of the processor that they exploit: "Ryzenfall," "Masterkey," "Fallout," and "Chimera."
The researchers "believe that networks that contain AMD computers are at a considerable risk," and that malware can "survive computer reboots and re-installations of the operating system, while remaining virtually undetectable by most endpoint security solutions," such as antivirus software. They also mention that in their opinion, "the basic nature of some of these vulnerabilities amounts to complete disregard of fundamental security principles. This raises concerning questions regarding security practices, auditing, and quality controls at AMD."
1. "Masterkey": This is an exploit of the Secure Boot feature, which checks if nothing has been tampered with on your machine while it was powered down (i.e. changes in firmware, hardware, or the last software state before shutdown). The Masterkey vulnerability gets around this environment integrity check by using an infected system BIOS, which can be flashed even from within Windows (with administrative privileges). Theoretically, Secure Boot should validate the integrity of the BIOS, but apparently this can be bypassed, exploiting bugs in the Secure Processor's metadata parsing. Once the BIOS signature is out of the way, you can put pretty much any ARM Cortex A5 compatible code into the modified BIOS, which will then execute inside the ARM-based Secure Processor - undetectable to any antivirus software running on the main CPU, because the antivirus software running on the CPU has no way to scan inside the Secure Processor.
2. "Ryzenfall" is a class of vulnerabilities targeting Secure Processor, which lets a well-designed malware stash its code into the Secure Processor of a running system, to get executed for the remainder of the system's up-time. Again, this attack requires administrative privileges on the host machine, but can be performed in real-time, on the running system, without modifying the firmware. Secure Processor uses system RAM, in addition to its own in-silicon memory on the processor's die. While this part of memory is fenced off from access by the CPU, bugs exist that can punch holes into that protection. Code running on the Secure Processor has complete access to the system; Microsoft Virtualization-based Security (VBS) can be bypassed and additional malware can be placed into system management storage, where it can't be detected by traditional antivirus software. Windows Defender Credentials Guard, a component that stores and authenticates passwords and other secure functions on the machine, can also be bypassed and the malware can spread over the network to other machines, or the firmware can be modified to exploit "Masterkey", which persists through reboots, undetectable.
3. "Fallout": This class of vulnerabilities affects only AMD EPYC servers. It requires admin privileges like the other exploits, and has similar effects. It enables an attacker to gain access to memory regions like Windows Isolated User Mode / Kernel Mode (VTL1) and Secure Management RAM of the CPU (which are not accessible, even with administrative privileges). Risks are the same as "Ryzenfall", the attack vector is just different.
4. "Chimera": This class of vulnerabilities is an exploitation of the motherboard chipset (e.g. X370 also known as Promontory). AMD outsourced design of their Ryzen chipsets to Taiwanese ASMedia, which is a subsidiary of ASUS. You might know the company from the third-party USB 3.0 and legacy PCI chips on many motherboards. The company has been fined for lax security practices in the past, and numerous issues were found in their earlier controller chips. For the AMD chipset, it looks like they just copy-pasted a lot of code and design, including vulnerabilities. The chipset runs its own code that tells it what to do, and here's the problem: Apparently a backdoor has been implemented that gives any attacker knowing the right passcode full access to the chipset, including arbitrary code execution inside the chipset. This code can now use the system's DMA (direct memory access) engine to read/write system memory, which allows malware injection into the OS. To exploit this attack vector, administrative privileges are required. Whether DMA can access the fenced off memory portions of the Secure Processor, to additionally attack the Secure Processor through this vulnerability, is not fully confirmed, however, the researchers verified it works on a small number of desktop boards. Your keyboard, mouse, network controllers, wired or wireless, are all connected to the chipset, which opens up various other attack mechanisms like keyloggers (that send off their logs by directly accessing the network controller without the CPU/OS ever knowing about these packets), or logging all interesting network traffic, even if its destination is another machine on the same Ethernet segment. As far as we know, the tiny 8-pin serial ROM chip is connected to the CPU on AMD Ryzen platform, not to the chipset or LPCIO controller, so infecting the firmware might not be possible with this approach. A second backdoor was found that is implemented in the physical chip design, so it can't be mitigated by a software update, and the researchers hint at the requirement for a recall.
AMD's Vega GPUs use an implementation of the Secure Processor, too, so it is very likely that Vega is affected in a similar way. An attacker could infect the GPU, and then use DMA to access the rest of the system through the attacks mentioned above.
The researchers have set up the website
AMDFlaws.comto chronicle these findings, and to publish detailed whitepapers in the near future.
AMD provided us with the following statement: "At AMD, security is a top priority and we are continually working to ensure the safety of our users as new risks arise. We are investigating this report, which we just received, to understand the methodology and merit of the findings."
Source: Many Thanks to Earthdog for the tipMore details have emerged about the new F1 Live OTT platform, as outlined by F1’s head of marketing Ellie Norman, who describes the boldness of the project as ‘pretty insane’.
Typing the words ‘F1’s head of marketing’ still feels slightly strange, seeing as for decades it was the only global Tier 1 sport that did not even have a marketing department, let alone a head.
Bernie Ecclestone used to rely on manufacturers, race promoters and sponsors to market the sport of Formula 1 for him. This kept the overheads down on the F1 Management side, while Ecclestone gleefully whipped up regular media attention by lobbing in regular hand grenades, which the newspapers gratefully jumped on.
Now it’s all rather different, although the infrastructure to make the new F1 Live OTT platform was all put in place by Ecclestone. He just chose not to use it for that, as he was all about protecting the rights of his broadcast partners.
Norman was previously at cable TV supplier Virgin Media and believes that the nature of the modern consumer who has a passion point is “… that passion tends to overrule the rational side of things; it is not uncommon if you have a pay TV bundle that you will have one or two of the top subscriptions. I think that with consumer behaviour and the desire to buy things you love, consumers are making that choice. If you are interested you will pay.”
That is the calculation; that of the potential audience for F1, identified at 500 million sports fans around the world, even if 1% of them paid their $8 a month for the OTT service, that would yield $40m a month, or almost half a billion dollars a year.
There is also the opportunity to upsell the packages in future; a Lewis Hamilton fan in Delhi could access more rich content about Hamilton and he could take a revenue share. There is also great value to F1 and its partners from the data that would be gathered about the consumers.
But for now it’s all about going direct to the fans and to make the fans’ access to F1 as frictionless as possible.
“Everyone is offering fans more direct access, we are incredibly fortunate with the access that we have through our sport,” Norman (above) said in an interview with digital media title The Drum. “We are going direct to the fan so we are then able to give them the best experience possible,” she told The Drum. There is nowhere else out there with 24 livestreams coming into the app and that is pretty insane – I don’t think that has been done before.”
“It is a very strategic sport and for that hardcore fan, they really understand the excitement but the strategic elements, having the ability to personalise how you watch it and being able to select favourite drivers and view that side by side, these are all elements where we can better serve our fans.”
The F1 OTT service will be rolled out in about two dozen countries, including USA, France, Germany and some Latin American markets – those where F1 has not ceded the digital rights to TV broadcast partners. That is the case in UK and Italy where Sky has the rights. F1 is talking to Sky about bundling the OTT rights.
What do you think of the F1 OTT platform and if you live in an eligible country, will you buy it? Leave your comments below
![[H]ardOCP: Crash Bandicoot Is Coming to the PC on July 10th](https://images.hardocp.com/images/hardocp_tw-fb-logo.jpg)
Come summer, the Crash Bandicoot: N-Sane Trilogy will no longer be a Sony exclusive: Activision has announced that the classic platforming games will land on PC, as well as Xbox One and Nintendo Switch, on July 10. The trilogy comprises Crash Bandicoot, Crash Bandicoot 2: Cortex Strikes Back, and Crash Bandicoot 3: Warped.
Somebody asked a few months ago “hey, what’s the best way to understand computer networking?”. I don’t really know how to answer this question – I’ve learned a lot of the things I know at work, and I think picking up new things when I need them has been fine.
But I thought it could maybe be useful to list a bunch of concrete skills and concepts I’ve learned along the way. Like anything else, “computer networking” involves a large number of different concepts and skills and tools and I’ve learned them all one at a time. I picked most of these things up over the last 4 years.
tcpdump in somewhat weird ways (for instance “only this very specific kind of DNS response”)openssl x509). here’s a blog post about TLSPer this tweet:
ip command. replacement for ifconfig. very useful.)nsenter for debugging container networking problemsI spend a fair amount of time trying to learn new computer things. I’ve found it really useful to take it one step at a time – my learning process with a lot of this stuff is basically
That’s all! It’s really fun to see how learning a bunch of tiny things adds up over time. Like today I feel like I can handle most things about computer networking that I run into in my job, and I don’t feel like there are that many Big New Ideas about networking I don’t know about. (though, well, wifi is still a mystery to me :) )
Intel developers are working on bringing transparent memory encryption support to the Linux kernel that works in conjunction with upcoming Intel platforms.
AMD's current EPYC and Ryzen Pro processors feature Secure Memory Encryption (SME) while upcoming Intel CPUs are working on a roughly similar feature with Total Memory Encryption (TME) along with MKTME, or Multikey Total Memory Encryption.
MKTME is built on top of TME. TME allows encryption of the entirety of system memory using a single key. MKTME allows to have multiple encryption domains, each having own key -- different memory pages can be encrypted with different keys.
Key design points of Intel MKTME:
- Initial HW implementation would support upto 63 keys (plus one default TME key). But the number of keys may be as low as 3, depending to SKU and BIOS settings.
Kirill Shutemov of Intel Finland today sent out
the initial kernel patchesfor this TME/MKTME kernel support code. In its present form is just over 500 lines of code to take advantage of this hardware-based transparent memory encryption for future Intel CPUs.

There's no better way to protect yourself from the universal scourge of phishing attacks than with a hardware token like a Yubikey, which stymies attackers even if you accidentally hand them your username and password. But while Yubikey manufacturer Yubico describes its product as "unphishable," a pair of researchers has proven the company wrong, with a technique that allows clever phishers to sidestep even Yubico's last bastion of login protection.
Two weeks ago, in a little-noticed presentation at the Offensive Con security conference in Berlin, security researchers Markus Vervier and Michele Orrù detailed a method that exploits a new and obscure feature of Google's Chrome browser to potentially bypass the account protections of any victim using the Yubikey Neo, one of the most popular of the so-called Universal Two-Factor, or U2F, tokens that security experts recommend as the strongest form of protection against phishing attacks.
With a sufficiently convincing phishing site and a feature in Chrome known as WebUSB, a hacker could both trick a victim into typing in their username and password—as with all phishing schemes—and then also send a query directly from their malicious website to the victim's Yubikey, using the response it provides to unlock that person's account. (A disclaimer: WIRED partners with Yubico to give free Yubikeys to subscribers. According to Vervier and Orrù, the model WIRED offers is not susceptible to their attack.)
Vervier and Orrù, who work for the security consultancy X41, are careful to note that their technique doesn't demonstrate a flaw in Yubico's products so much as a very unintended byproduct of Chrome's WebUSB feature, which the browser added just last year. "U2F is technically not broken, but it’s still phishable, which many people thought was impossible," says Vervier. "It’s a great example of how new interfaces allow ways to attack technology that were believed to be unbreakable."
When WIRED reached out to Google, security product manager Christian Brand responded that the company became aware of the researchers' attack after their Offensive Con presentation. While Google considers the attack an edge case, the company is working with U2F standards body the FIDO Alliance to fix the problem. "We are always appreciative of researchers’ work to help protect our users," Brand wrote in a statement. "We will have a short term mitigation in place in the upcoming version of Chrome, and we're working closely with the FIDO Alliance to develop a longer-term solution as well. We aren’t aware of any evidence that the vulnerability has been exploited."
Let's be clear: Vervier and Orrù's findings don't change the fact that adding two-factor authentication remains one of the most basic and crucial steps to protecting your sensitive accounts, and a U2F token like a Yubikey is the most secure form of that protection you can use. Even two-factor authentication methods like text messages or Google Authenticator still rely on temporary codes that the user enters when they log in; a convincing phishing site can simply trick you into handing over those codes along with your username and password. A U2F token like the Yubikey instead performs an authentication handshake with a website that not only proves to a website that it's your unique key, but requires that the website prove its identity too, preventing lookalike sites from stealing credentials.
'They put in another feature that subverts all the security they'd put in place.'
Joern Schneeweisz, Recurity Labs
But a crack in those safeguards may have appeared last year when Chrome added WebUSB, a feature that allows websites to directly connect to USB devices, from VR headsets to 3-D printers. Vervier and Orrù found that they could code a website to connect to the Yubikey Neo with that WebUSB feature, instead of with the usual Chrome API for U2F that it's designed to use. In doing so, they could circumvent the checks that the browser performs before querying the Yubikey—the checks that confirm that websites are the ones they claimed to be.
That could enable, the researchers warn, a "man-in-the-middle" attack. If a victim logs into a fake Google site, the phishing site passes on their username and password to the real Google login page. Then the spoofed site passes back Google's request for the user's U2F token and collects the Yubikey's unique answer, all via WebUSB. When that answer is then presented to the real Google site, the attackers gain access to the victim's account.
"The browser developers put a proper API in place that makes careful use of whatever U2F token is in the computer," says Joern Schneeweisz, a security researcher for Recurity Labs who reviewed Vervier and Orrù's findings. "And then they put in another feature that subverts all the security they'd put in place."
The attack Vervier and Orrù imagine isn't exactly easy to pull off, and would likely only be used by sophisticated hackers targeting high-value accounts. Aside from first requiring that a phishing site trick a victim into typing in their username and password as usual, the phishing site would also have to ask the user's permission to enable WebUSB access to their Yubikey, and then tap the physical button on the key. But all of that could be achieved by phishers who trick users with a prompt requiring them to "update" their U2F token, or some other scam. After all, the only change from the usual login process would be that one added permissions prompt. "You could come up with a pretty plausible pretext," says Orrù. "The user only has to click once."
Vervier and Orrù note that their technique would only work with U2F keys that offer protocols for connecting to a browser other than the usual way U2F tokens communicate with a computer, known as the Human Interface Device or HID, which isn't vulnerable to the attack. The Yubikey Neo, for instance, can also connect via the CCID interface used by smartcard readers, offering another avenue of exploitation, but the Yubikey Nano, 4 Series, and the original, cheaper Yubikey aren't vulnerable, they say—nor, based on their testing, were the Feitian keys recommended by Google for its locked-down Advanced Protection setting.
"This sounds like an assumption was made by Chrome that all U2F is HID, which doesn't hold for the Neo, whereas Yubico made an assumption that USB will never be accessible by web pages directly," explains Jonathan Rudenberg, an independent security researcher who has focused on U2F implementations in the past. The combination of those two assumptions adds up to a significant security vulnerability.
A long-term fix could take the form of tweaks to Chrome to block WebUSB connections to certain devices like the Yubikey Neo. But the problem could go much further than Yubikeys alone, potentially exposing a whole new class of devices to unexpected interactions with websites. Vervier and Orrù say they believe smartcard authentication systems could also be vulnerable, for instance, though they haven't yet tested them.
"Google should have never shipped WebUSB in its current form," says Rudenberg. "Users cannot be expected to understand the security implications of exposing their USB devices to potentially malicious code...I don’t think this is the last time that we’ll see WebUSB used to break things." Rudenberg went so far as to quickly code a Chrome extension that disables WebUSB, which he recommends everyone install and use until they have a reason to enable the feature. Rudenberg says there's no other easy way to disable the feature.
'Google should have never shipped WebUSB in its current form.
Security Researcher Jonathan Rudenberg
When WIRED reached out to Yubico for comment, spokesperson Ronnie Manning essentially placed the blame on Google's browser. "Per the U2F protocol, the security key is not responsible for doing that verification" of the origin of authentication requests, Manning said in a statement. "In fact, they cannot do so effectively as they would have to rely on data passed by the browser, and if the browser is not trustworthy, neither is the data."
Manning also noted that Chrome could give users the option to turn off WebUSB, or blacklist vulnerable devices like the Yubikey Neo. But he adds that "unless such a blacklist is complete and perfect, issues like this are possible with the current WebUSB implementation."
As for Vervier and Orrù themselves, they say concerned Yubikey users should disable WebUSB, and that IT administrators should even consider setting a policy blocking it for all their employees. And they suggest a simpler solution, too: That users remain wary online, and think twice about where they enter their passwords. Despite Yubico's "unphishable" marketing, it's no substitute for some healthy skepticism.
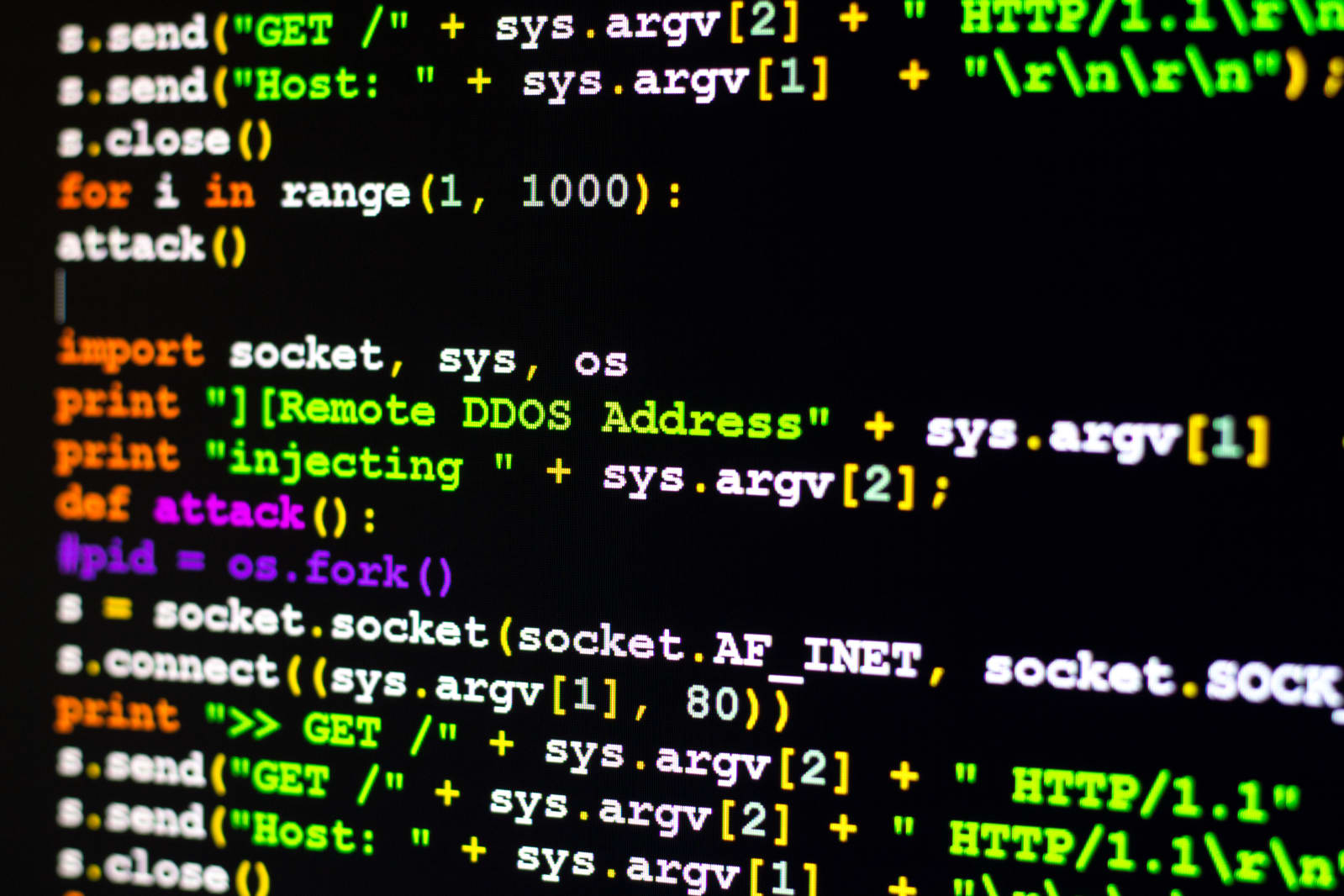
GitHub, a web-based code distribution and version control service, survived a massive denial of service attack on Wednesday. According to a report at Wired, a staggering 1.35 terabits per second (Tbps) of traffic hit the site at once. Within 10 minutes the company called for help from a DDoS mitigation service similar to Google's Project Shield, Akamai's Prolexic, which took over to filter and weed out malicious traffic packets. The attack, says Wired, ended after eight minutes. This may have been the largest DDoS attack ever; Wired notes the attack on domain name server Dyn in late 2016 reached 1.2 Tbps of traffic.
The attack was apparently conducted via a non-bot technique called an amplification attack. These use memcached database systems, says Wired, that can be queried by anyone. Attackers spoof the IP of their target and send small requests to the memcached databases, which then send a massive amount of traffic to the target system, like GitHub in this case. The answer to shutting down attacks like these is twofold, says Wired. Mitigation services like Prolexic can add filters to automatically block this sort of traffic, and owners of memcached databases can remove them from public access.
Source: Wired
Honestly, if it can be described as "a #{beloved_service} client for your terminal", I'm gonna log it.
This is a simplified clone of Pocket, written in Go. It can be used as a command-line app, or from the web. It's distributed as a single binary, which means installs are easy, peasy.
I was clueless about this until I saw the Smashing Mag headline in my feedbin:
Europe’s imminent privacy overhaul means that we all have to become more diligent about what data we collect, how we collect it, and what we do with it.
Read through and be aware of the implications. These changes become enforceable in May of 2018.

Over the next few years, select Lego pieces will start being made with plant-derived materials as part of the company's pledge to create more sustainable products. Parts resembling leaves, bushes and trees will be made from a polyethylene created with ethanol made from sugarcane. And while these only make up between 1 and 2 percent of all the pieces Lego makes, it's "a great first step in our ambitious commitment of making all Lego bricks using sustainable materials," Lego VP of environmental responsibility Tim Brooks said on its website. These 'green' pieces will be released in sets starting this year.
Give your biggest "green" to the very FIRST #sustainable LEGO Bricks! LEGO botanical elements including leaves and trees will now be made from sugarcane-based plastic.The first "greens" are to appear in LEGO sets later this year. Sweeet🌿#PlantsfromPlants https://t.co/rZKijykjYO pic.twitter.com/yraEOLq5NM
— LEGO (@LEGO_Group) March 1, 2018
It's part of the company's pledge to transition to using sustainable materials in Lego products and packaging by 2030. Creating plastic parts from sugarcane -- called 'bioplastics' -- isn't a perfect solution, as that crop still requires a lot of farmland, and growing more could cut into land allocated for food production. Further, the historical demand for sugarcane has degraded tropical forests and coastal wetlands; More demand could lead to further deforestation.
Changing the Lego recipe from acrylonitrile butadiene styrene (based on crude oil) to a plant-sourced plastic is certainly a more sustainable choice. And though sugarcane isn't a perfect source for bioplastics, it's a first step toward making your favorite building toys (and future domestic caltrops) a little greener.
Via: BBC
Source: Lego